A scareware campaign phishing for login credentials recently switched from targeting Windows to macOS, Israeli cybersecurity firm LayerX reports.
Throughout 2024 and in early 2025, the attacks targeted Windows users, relying on compromised websites to serve fake Microsoft security alerts claiming that users’ computers had been compromised and locked.
The malicious code caused the webpages to freeze, creating the illusion of an issue, and the victim was instructed to provide their Windows username and password, LayerX explains.
As part of the campaign, the threat actors hosted their phishing pages on the legitimate Azure application hosting platform Windows.net, adding a sense of legitimacy to the fake prompts.
The use of a trusted hosted service for the underlying infrastructure allowed the attackers to bypass anti-phishing defenses that check the reputation of the Top-Level Domain (TLD).
“In this case, the TLD (windows[.]net) is a well-known and highly-used platform by a reputable provider (Microsoft), with a high TLD reputation score. As a result, these pages were able to circumvent traditional protection mechanisms,” LayerX explains.
Randomized, rapidly-morphing subdomains were also used to serve malicious code, and the attackers carefully crafted their phishing pages to look as professional as possible, and included anti-bot and CAPTCHA verification on them, likely to delay automated page classification solutions.
Recently, Chrome, Firefox, and Microsoft Edge received new anti-scareware capabilities, which led to a 90% drop in Windows-targeted attacks, and forced the threat actors to switch focus to macOS users, who are not protected by these defense mechanisms.
While no attack against macOS was observed while the Windows campaign was ongoing, within two weeks after the new anti-phishing defenses were rolled out, the first attacks against macOS users started, LayerX says.
The phishing pages were nearly identical to those used in the Windows attacks, and continued to be hosted on Windows[.]net, but the layout and messaging were tailored for macOS users, and the malicious code was modified to target Safari.
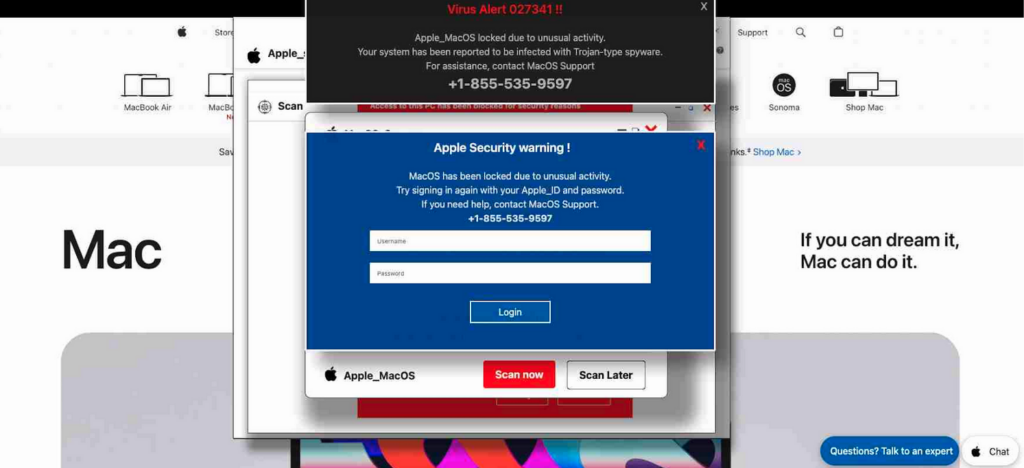
According to LayerX, victims incorrectly typing the URL for a legitimate website were taken to compromised domain ‘parking’ pages and then redirected through multiple domains to finally be served a phishing page.
“In one specific case, the victim was a macOS and Safari user working for a LayerX enterprise customer. Despite the organization employing a Secure Web Gateway (SWG), the attack bypassed it,” the cybersecurity firm explains.
LayerX believes that the attackers may further adapt their campaign after making macOS users on Safari their prime targets with minimal modifications to the existing infrastructure, and underlines that this campaign may pose a significant risk to enterprise users.
“Whereas the compromise of a personal, non-corporate account is typically limited to the exposure of that individual user, the compromise of a corporate/enterprise account can result in data exposure at the organizational level, making the threat much more severe,” LayerX head of product marketing Eyal Arazi told SecurityWeek.
“As the change of attack vectors from Windows to Mac demonstrates, this campaign is a highly professional, persistent, and adaptive attack campaign, which poses significant threats to enterprise users,” he said.
Related: Microsoft 365 Targeted in New Phishing, Account Takeover Attacks
Related: Russian State Hackers Target Organizations With Device Code Phishing
Related: Fake DeepSeek Sites Used for Credential Phishing, Crypto Theft, Scams
Related: PayPal Phishing Campaign Employs Genuine Links to Take Over Accounts


