Threat actors are abusing a weakness in Google Sites to deliver sophisticated phishing emails that bypass email authentication checks.
As part of the campaign, recipients receive email messages that appear to come from a legitimate Google no-reply address, and which redirect them to Google Sites pages that mimic official Google pages.
Two attacks flagged by Ethereum Foundation developer Nick Johnson and EasyDMARC CEO Gerasim Hovhannisyan show that the attackers are abusing vulnerabilities in Google Sites, a legacy service that allows anyone to build custom websites hosted on the sites.google.com domain.
Because the site is hosted under a trusted Google-owned domain, it benefits from the internet giant’s SSL certificates and brand reputation, allowing the attackers to embed deceptive content that passes validation checks and user trust, Hovhannisyan notes.
To mount an attack, the threat actor registers a website and creates an account for it; then they forward a legitimate email received from Google without modifying the content and headers covered by its DKIM signature, to ensure it can bypass protections.
The attack targeting Johnson used an account for me@[attacker domain] and a Google OAuth application that had the entire phishing message as its name, and forwarded a security alert message sent to their ‘me@…’ email address.
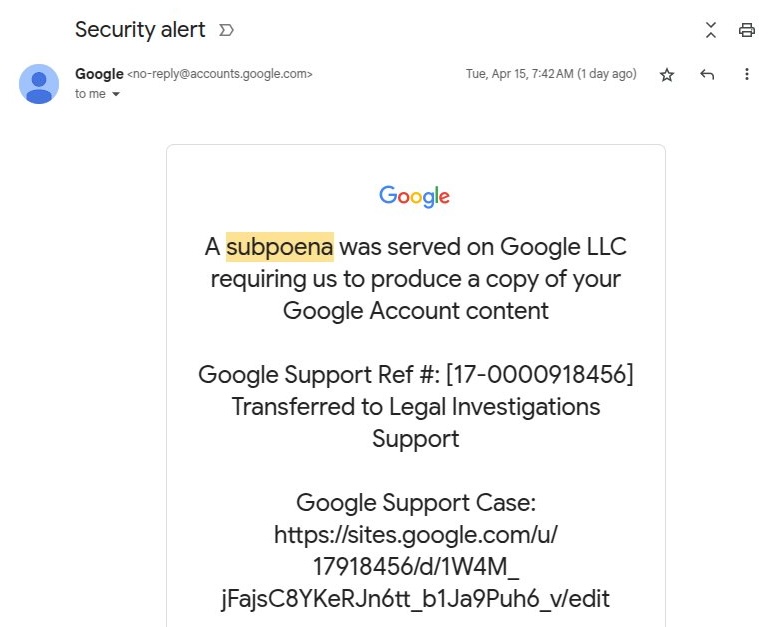
“Because DKIM only verifies the message and its headers and not the envelope, the message passes signature validation and shows up as a legitimate message in the user’s inbox – even in the same thread as legit security alerts,” Johnson explains.
Furthermore, because the account was named ‘me@’ Gmail displayed the message as being sent to ‘me’ as it would typically show when sent to the recipient’s address.
Google was notified of the OAuth security defect abused in these attacks and will address it, after initially dismissing it as ‘Working as Intended’, Johnson says.
Related: AI Now Outsmarts Humans in Spear Phishing, Analysis Shows
Related: CRM, Bulk Email Providers Targeted in Crypto Phishing Campaign
Related: Morphing Meerkat Phishing Kits Target Over 100 Brands
Related: Browser Security Under Siege: The Alarming Rise of AI-Powered Phishing


