The SANS Institute and OPSWAT on Tuesday published the 2025 ICS/OT Cybersecurity Budget Report.
The report, based on a survey of 180 individuals representing critical infrastructure sectors around the world, shows that over a quarter of organizations have experienced one or more security incidents involving OT or control systems in the past year. It’s worth noting that the actual percentage is likely higher considering that 11% were unsure and nearly 20% were unable to answer due to company policy.
The most common initial attack vector was a compromise in the IT environment that allowed the attacker to move to the OT network (57%). Other common initial attack vectors were internet-accessible devices (33%), and hacked engineering workstations (30%).
The survey showed that 55% of organizations saw a budget increase — including a significant raise in 23% of cases — in the past two years. Only 5% reported a minor decrease in their ICS/OT security budget.
Unsurprisingly, the bigger the company, the bigger the budget for protecting industrial control and other operational technology systems, but even some small companies reported having an annual budget that exceeds $100,000.
Save the date: 2025 ICS Cyber Security Conference – October 27-30, Atlanta
Despite the importance of securing ICS and OT in critical infrastructure organizations, the survey identified several issues.
For instance, only 9% of respondents dedicate all of their time to ICS/OT security, and on average only 52% of time is dedicated to this task.
In addition, in roughly one quarter of cases the ICS/OT security budget is controlled by enterprise IT and in one-third of cases the budget is shared between IT and OT.
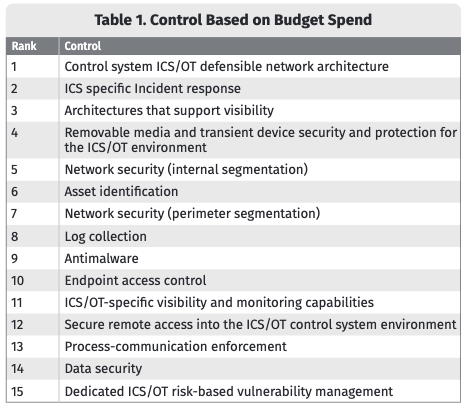
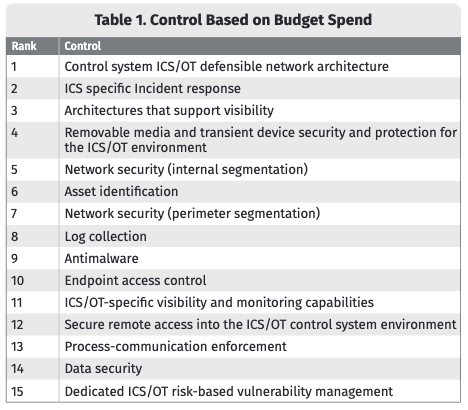
In terms of what the budget will be spent on, the number one response was ICS/OT defensible network architecture, followed by incident response, and architectures that support visibility. However, the survey shows that some important areas remain underfunded.
“ICS Network Visibility and Monitoring, crucial for detecting threats, identifying vulnerabilities safely, and aiding engineering network troubleshooting, ranks lower, despite its high ROI,” explained the authors of the report. “Secure Remote Access, essential for preventing unauthorized access in increasingly remote operations, remains underfunded, despite rising attacks on unsecured connections.”
The complete 2025 ICS/OT Cybersecurity Budget Report is available in PDF format.
Related: Nine Threat Groups Active in OT Operations in 2024: Dragos
Related: Free Diagram Tool Aids Management of Complex ICS/OT Cybersecurity Decisions
Related: Cyber Insights 2025: OT Security