Google’s Threat Intelligence Group on Tuesday published its analysis of zero-day vulnerability exploitation for 2024.
A zero-day is a vulnerability that has been exploited in the wild before a patch was released to the public. This is the definition used by Google and many others in the industry, but some individuals and cybersecurity companies have different definitions, in some cases referring to any new vulnerability — even if it has not been exploited — as a zero-day.
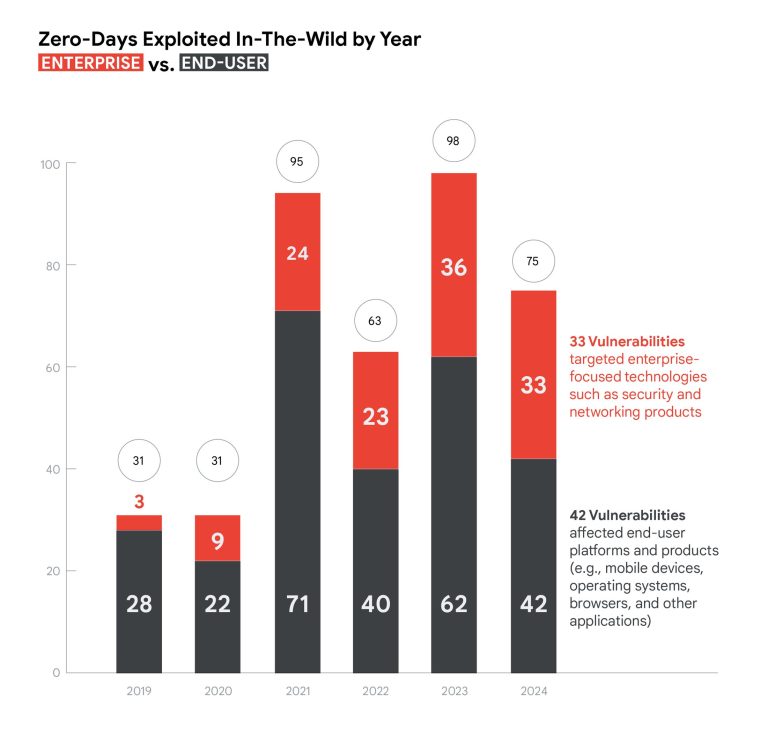
The internet giant reported tracking 75 zero-day vulnerabilities in 2024, a decrease from the 98 observed in 2023, but still more than the 63 spotted in 2022.
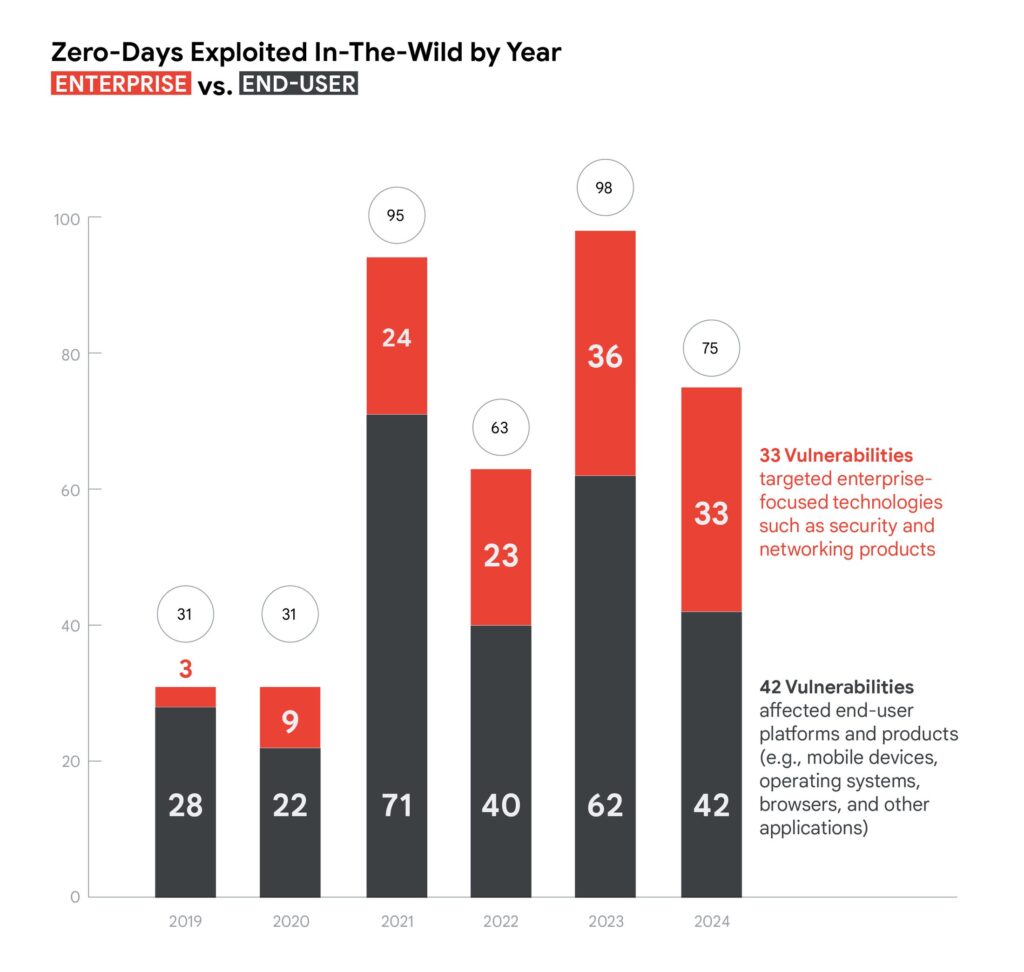
Of the 75 zero-days seen last year, 33 impacted enterprise technologies such as networking and security products, while the rest affected end-user products such as browsers, operating systems and mobile devices.
In the case of end-user products, Google observed an increase in Windows exploits and a significant drop in Safari and iOS exploits. Chrome remained the most targeted browser, which Google says is an indication of its massive popularity.
The company also reported that roughly 90% of the exploits chaining multiple vulnerabilities were aimed at mobile devices. In the case of Android, a significant percentage of exploits targeted third-party components.
As for enterprise products, Google pointed to the targeting of Ivanti, Palo Alto Networks, and Cisco appliances, and explained why they can represent a tempting target for threat actors.
“Endpoint detection and response (EDR) tools are not usually equipped to work on these products, limiting available capabilities to monitor them. Additionally, exploit chains are not generally required to exploit these systems, giving extensive power to individual vulnerabilities that can single-handedly achieve remote code execution or privilege escalation,” the company said.
As for who was behind the exploitation of zero-days in 2024, Google was able to find links to known threat actors in the case of 34 of the 75 exploits. Nearly 45% were attributed to state-sponsored threat actors that used them for espionage or financially motivated attacks.
Nearly a quarter of the 34 zero-days were linked to commercial surveillance vendors, and roughly 30% were linked to non-state financially motivated groups.
Additional information and trends are available in Google’s full report (PDF).
Related: Exploited Vulnerability Exposes Over 400 SAP NetWeaver Servers to Attacks
Related: Craft CMS Zero-Day Exploited to Compromise Hundreds of Websites
Related: South Korean Companies Targeted by Lazarus via Watering Hole Attacks, Zero-Days