Scans show that tens of thousands of VMware ESXi instances are affected by the vulnerabilities disclosed recently as zero-days.
On March 4, VMware owner Broadcom informed ESXi, Workstation, and Fusion customers about the availability of patches for three zero-days exploited in the wild. Their exploitation can lead to arbitrary code execution, sandbox escapes, and memory leaks.
The flaws are tracked as CVE-2025-22224, CVE-2025-22225 and CVE-2025-22226, and they can allow attackers with elevated privileges to perform a VM escape.
“This is a situation where an attacker who has already compromised a virtual machine’s guest OS and gained privileged access (administrator or root) could move into the hypervisor itself,” Broadcom explained.
The company has credited Microsoft Threat Intelligence Center for reporting the vulnerabilities — Microsoft likely also saw the attacks exploiting the zero-days — but neither Broadcom nor Microsoft have shared any information on the attacks.
The cybersecurity agency CISA has added the flaws to its Known Exploited Vulnerabilities (KEV) catalog, which now includes nearly 30 VMware product vulnerabilities.
Netlas has reported seeing more than 7,000 internet-exposed VMware ESXi instances that appear to be impacted by the vulnerabilities.
The Shadowserver Foundation has reported seeing more than 41,000 vulnerable ESXi instances, a majority in China, France, the US, Germany, Iran, Brazil and South Korea.
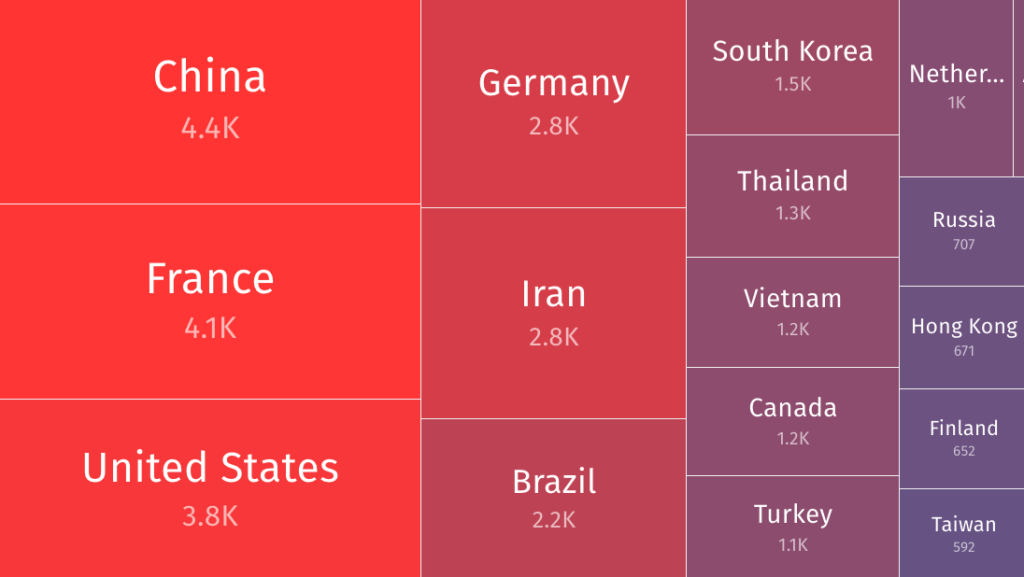
The scans conducted by Shadowserver target CVE-2025-22224, but these instances are likely affected by the other vulnerabilities as well since they all impact the same software versions.
Technical details and a PoC exploit do not appear to be available for CVE-2025-22224, CVE-2025-22225 and CVE-2025-22226 — this would make it easier for more threat actors to exploit the vulnerabilities — giving organizations more time to install the patches before widespread exploitation commences.
Security researcher Kevin Beaumont, who has dubbed the vulnerabilities ESXicape, explained, “Once you have ESX access, you can access everything on the ESX server — which includes things such as VM data, and crucially ESX config and mounted storage. Using ESX config and mounted network storage, you can traverse the VMware environment.”
Beaumont added, “For example, orgs use vMotion to allow virtual machines to automatically move across ESX hosts, to balance load and allow for maintenance without downtime (it’s how VMware security patching works). Because of this, a threat actor has direct access to storage of VMs both on and not on that host by design — they’re basically loose on the backend.”
According to the researcher, threat actors could use the vulnerabilities to get past security products and gain access to valuable assets such as Active Directory domain controller databases without triggering alerts. This could be useful in ransomware attacks.
“This is frequently seen in ransomware incidents, where people directly exploit the ESX server or vCenter server over the VMware management network using unpatched vulnerabilities. Once they reach ESX, they reach directly into storage across the whole cluster,” Beaumont said, adding, “However, being able to reach the ESX server hypervisor directly from the Virtual Machine significantly raises the risk. For example, you don’t need to find the ESX server details, or reach a segregated network.”
Beaumont pointed out that a hacker recently offered to sell an ESXi VM escape exploit for $150,000, but it’s unclear if that was a genuine exploit and whether it’s related to the zero-day attacks disclosed this week.
Related: VMware Patches High-Risk Flaws in Oft-Targeted Aria Operations Products
Related: VMware Struggles to Fix Flaw Exploited at Chinese Hacking Contest
Related: VMware Discloses Exploitation of Hard-to-Fix vCenter Server Flaw


