Several cybersecurity organizations are tracking what has been described as one of the largest known DDoS botnets observed in recent years.
The new botnet, named Eleven11bot, was recently noticed by Nokia’s Deepfield Emergency Response Team, which saw hyper-volumetric DDoS attacks conducted by its operators.
Nokia reported on February 28 that Eleven11bot had ensnared roughly 30,000 devices, mainly security cameras and network video recorder (NVR) devices.
However, the non-profit cybersecurity organization Shadowserver Foundation reported on Tuesday that its scanning had identified approximately 86,400 IoT devices compromised by the botnet.
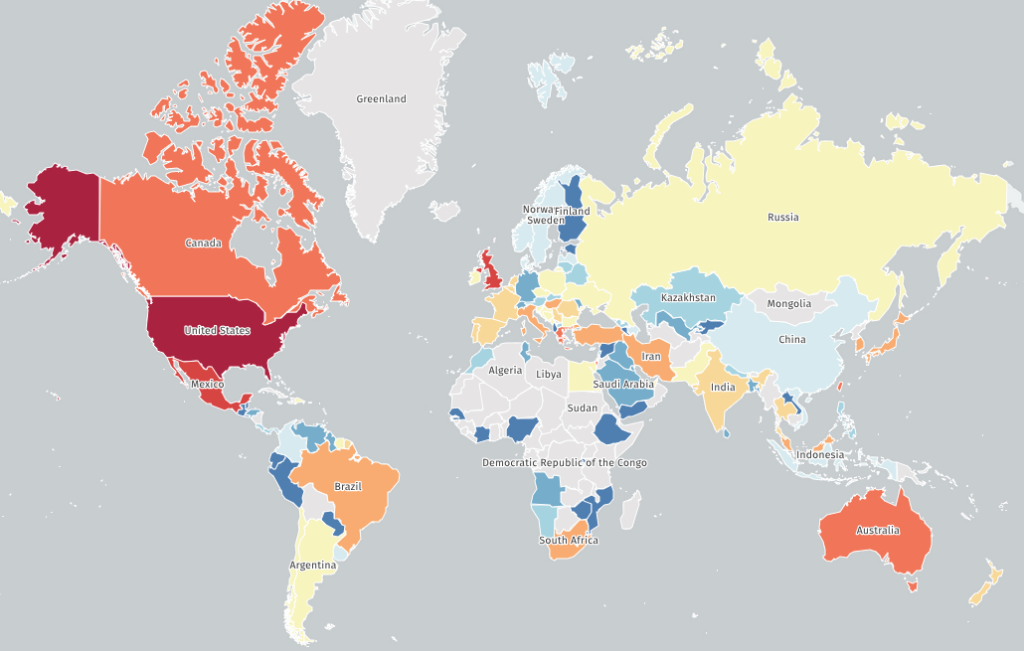
A majority of the impacted devices are in the United States (25,000), followed by the United Kingdom (10,000), Canada (4,000) and Australia (3,000).
“Its size is exceptional among non-state actor botnets, making it one of the largest known DDoS botnet campaigns observed since the invasion of Ukraine in February 2022,” said Nokia security researcher Jerome Meyer.
Eleven11bot has been observed launching DDoS attacks against various sectors, including gaming and communications, some attacks lasting for days and causing significant disruption.
“Attack intensity has varied widely, ranging from a few hundred thousand to several hundred million packets per second (pps),” according to Meyer.
Attack surface management firm Censys and threat intelligence company GreyNoise have also started tracking Eleven11bot.
Censys has seen 1,400 IPs linked to the botnet based on endpoint device configurations and banners, and GreyNoise has seen more than 1,000 IP addresses targeting its honeypots.
According to GreyNoise, 61% of the 1,000 IPs are Iranian. The company has refrained from making statements on attribution, but noted that “this increase in botnet activity comes just two days after the US administration reasserted its ‘maximum pressure’ campaign on Iran, imposing new economic sanctions”.
GreyNoise said Eleven11bot has been ensnaring new devices through brute-force attacks, the exploitation of weak or default IoT device passwords, and network scans targeting exposed SSH and Telnet ports.
Related: Chinese Botnet Powered by 130,000 Devices Targets Microsoft 365 Accounts
Related: Vo1d Botnet Evolves as It Ensnares 1.6 Million Android TV Boxes
Related: Aquabot Botnet Targeting Vulnerable Mitel Phones