At least 11 state-sponsored threat groups have been abusing Windows shortcut files for espionage and data theft, according to an analysis by Trend Micro’s Zero Day Initiative (ZDI).
Shortcut files, also referred to as LNK or .lnk files, use the Shell Link binary file format to store information for accessing other data objects. These LNK files can point to files, folders or applications.
However, for years threat actors have been using specially crafted LNK files that embed command-line arguments for Cmd or PowerShell that are designed to download and execute malware.
ZDI has identified nearly 1,000 malicious LNK files set up by state-sponsored threat groups and profit-driven cybercriminals to run hidden commands when executed.
It’s worth noting that victims are required to manually execute the malicious shortcut files to trigger the execution of the attacker’s commands. To achieve this, threat actors typically disguise the file as a harmless document or other type of file.
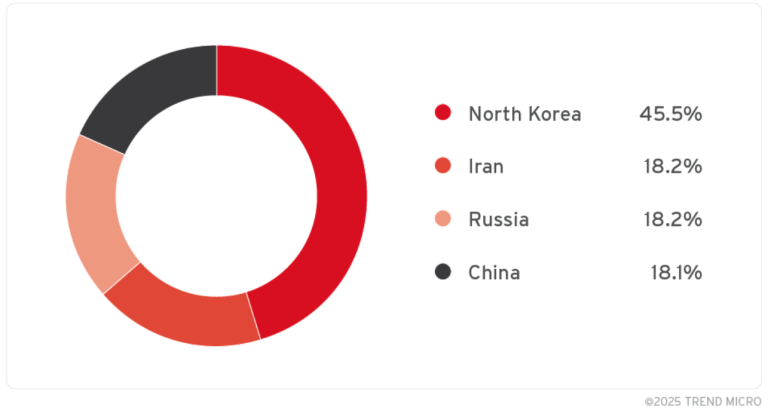
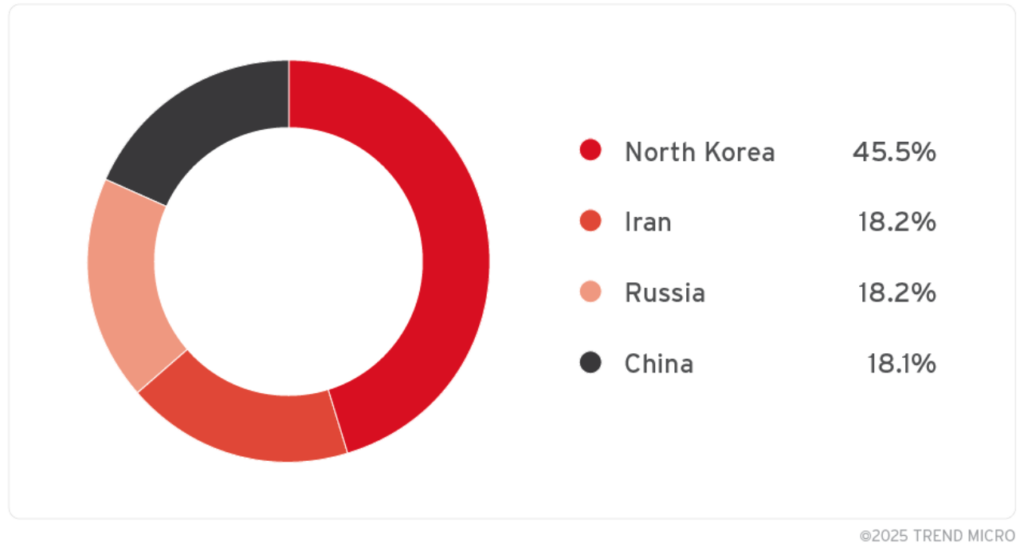
ZDI’s analysis has revealed that specially crafted LNK files have been used by 11 state-sponsored APT groups from North Korea, Russia, China, and Iran.
Targets included government, financial, think tank, telecoms, energy, military and defense, and private organizations in North America, Europe, Asia, South America, and Australia.
The hackers used the LNK files to deliver loaders and other types of malware, with the main objective often being cyberespionage or data theft.
The attackers rely on padding and large file sizes to prevent the targeted user from being able to easily determine the true intent of a LNK file.
ZDI describes this issue as user interface (UI) misrepresentation of critical information, arguing that the Windows UI fails to present the user with critical information. Third-party tools are, however, capable of allowing a thorough inspection of a LNK file, which would reveal the hidden commands.
ZDI was hoping to get a CVE identifier assigned to this issue, but it has yet to succeed and is currently tracking it as ZDI-CAN-25373. The company informed Microsoft about the risks in hopes that action would be taken, but said the tech giant assigned it a ‘low severity’ rating and indicated that it will not be addressed in the immediate future.
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
“Organizations should immediately scan and ensure security mitigations for ZDI-CAN-25373, maintain vigilance against suspicious .lnk files, and ensure comprehensive endpoint and network protection measures are in place to detect and respond to this threat,” ZDI recommends.
Related: Iranian Hackers Target UAE Firms With Polyglot Files
Related: Exploit Code for Apache Tomcat RCE Vulnerability Published on Chinese Forum
Related: ClickFix Widely Adopted by Cybercriminals, APT Groups